The honeypot scam poses a serious and insidious threat in the cryptocurrency world, preying on unsuspecting investors. These scams are carefully designed to lure investors into fraudulent projects, ultimately locking them out from accessing their own funds.
For crypto investors, understanding the mechanics and tactics of these honeypot scams is crucial to safeguarding their assets. Okay let’s dive into this further with crypto insights from FMCPAY!
1. What is a Honeypot Scam?
A honeypot refers to a smart contract intentionally designed with security vulnerabilities that are easy for users to spot and exploit. When users attempt to exploit these vulnerabilities, they fall into a “trap” set by certain hidden rules in the contract, ultimately resulting in the loss of their money.
For example, a scammer could create a smart contract with a security flaw that supposedly allows users to withdraw a large number of tokens if they first deposit a small amount into the contract. However, after making the deposit, users find that they cannot withdraw the tokens because the contract stipulates that only the contract creator has the authority to withdraw assets.

This makes honeypot scams a “trap within a trap,” tricking users into believing they can sneak in the assets within the contract, when in reality, they end up losing their own funds.
Additionally, the term “honeypot” has recently been used to describe scams or crypto projects that offer users lucrative rewards with the hidden intent of stealing their funds later on.
2. How Does a Honeypot Scam Crypto Work?
A honeypot scam in crypto typically involves smart contracts, which are self-executing contracts with the terms of the agreement directly written into code. These smart contracts are placed on blockchain networks, making them appear legitimate and transparent. However, scammers embed hidden conditions within the smart contract that act as traps for investors.
Here’s an example of how a honeypot scam unfolds:
- Creating the Trap: The scammer sets up a fake project, token, or investment opportunity and deploys a smart contract on a blockchain like Ethereum or BNB Chain. The project may even come with a polished website, a social media presence, and endorsements to appear credible.
- Luring the Preys: The scammers promote the trap using social media, influencers, community posts, or even paid advertisements to attract investors. They may promote the token’s low price and high growth potential, or launch big airdrop events to entice people to buy in.
- Flaw Exploitation: When investors buy the token or send their funds to the smart contract, they later discover that they cannot withdraw their assets or sell the token. The smart contract’s code may have a condition that prevents selling, restricts certain addresses from trading, or implements high fees that make withdrawal nearly impossible.
- Assets Withdrawal: Not only benefit from the prey’s deposited amount, the honeypot scammer may go even further to maximize their profits. While the victims struggle to recover their funds, the scammers either dump their pre-mined tokens on the market or siphon off the invested crypto. As the token’s value crashes, the scammers make a quick exit, leaving the investors with worthless assets.
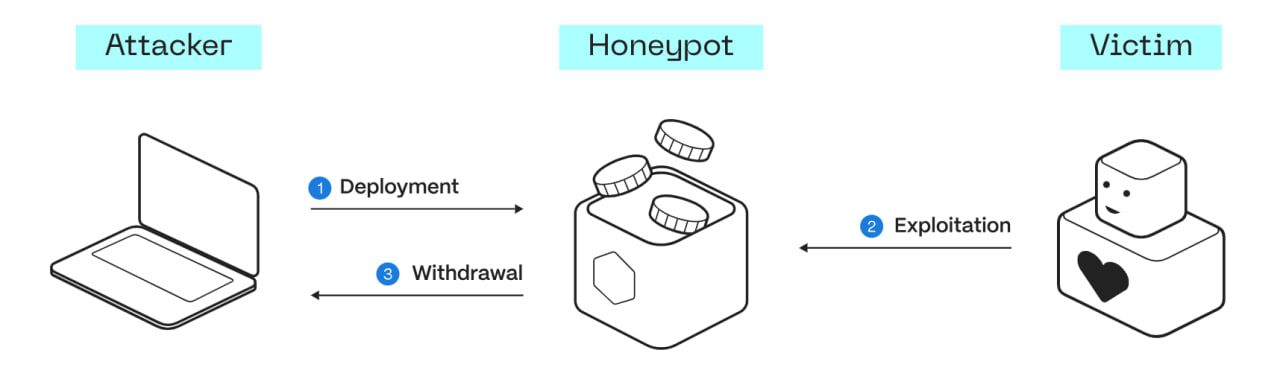
3. Some Popular Tactics of Honeypot Scams
A honeypot scam may apply various tactics to deceive and trap crypto investors. Understanding these tactics can help investors identify and avoid potential threats. Below are some popular methods used by scammers:
3.1. The Blacklist
In this type of honeypot scam, the smart contract has codes that allow anyone to buy the token but only addresses not on the blacklist can sell it. Scammers may blacklist the addresses of buyers after they have made their purchases, effectively trapping the victims’ funds.
This method is particularly difficult to detect because the buying function works smoothly, giving the impression that the token is legitimate. However, when investors try to sell their tokens, they find that their transactions are rejected due to their address being blacklisted.
3.2. The Manipulated Balance
A more deceptive tactic used in honeypot scams involves tampering with a user’s token balance. Rather than outright blocking users from selling, this method subtly changes the token balance to a fixed amount set by the scammer’s smart contract.
While users may still believe they hold their original number of tokens, the contract’s altered balance limits them to selling only the reduced amount. As a result, investors are trapped with tokens they can neither sell nor transfer, leaving their investment effectively worthless.
3.3. The Minimum Sell Amount
In this variation of the honeypot scam, the smart contract has a condition that only allows token sales above a certain minimum amount. This minimum amount is deliberately set at an extremely high threshold, far beyond the available token supply, making it practically impossible for investors to meet.
As a result, investors are trapped, unable to sell their tokens because the required amount is unachievable. Even if they attempt to buy more tokens to reach the threshold, the same restriction remains, leaving them unable to cash out or recover their investment.
4. Another New Honeypot Scam Variant in Crypto
A newer honeypot scam variant in the crypto space is the “Help me” scam, which also preys on the greed of crypto users. Here’s how it works:
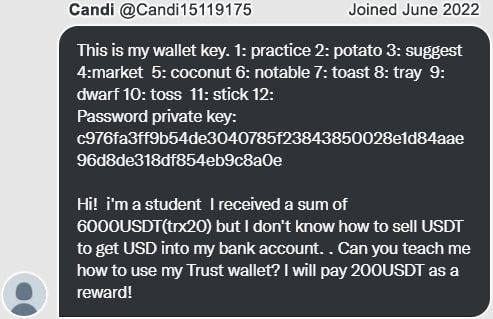
4.1. Initial Contact
In this variant, scammers pose as people in distress who need help withdrawing funds, completing a transaction, or accessing a wallet. They may reach out to potential victims through social media comments or Telegram group chat, sharing a story of hardship and requesting assistance.
They intentionally share details, including the wallet’s Secret Recovery Phrase (seed phrase), to lure the greedy prey into attempting to access the wallet and transfer all the funds out. If you think of something like “What a stupid, Imma go take all this easy money”, then you have stepped one leg into their trap.
4.2. Access the Wallet
Having the private key to a wallet holding $6,000 worth of tokens is tempting, but this is where things start to get complicated.
Usually, you will need the network’s native token as transaction fee (TRX in this example) to move the assets out to other wallets address. The scammer’s wallet may have lots of money but it lacks any TRX. This means that if you wanted to send them anywhere else, first you’d need to deposit in some TRC to pay the transaction fees.
So, let’s say you decide to send a small amount of TRX to Candi’s wallet to cover the transaction fees, with the goal of transferring the 6,000 USDT out. But as soon as you deposit the TRX, it disappears.
4.3. What just happened?
TRON blockchain is a network that supports the multi-sig feature. When we deposit fees into the above wallet to transfer money, the transaction cannot proceed because the multi-sig feature on the TRON network requires confirmation on at least 2 wallets.
Additionally, a script embedded in the contract is designed to steal any deposited tokens. As soon as you send tokens to the wallet for gas fees, a sweeper script (or sweeper bot) immediately transfers them to another address before you have a chance to make the transaction yourself.
The $6,000 funds they leave in the wallet as bait will stay there and never be touched. No one can ever transfer them out. If you were to view the honeypot wallet address on a blockchain explorer, you would notice a pattern like this:
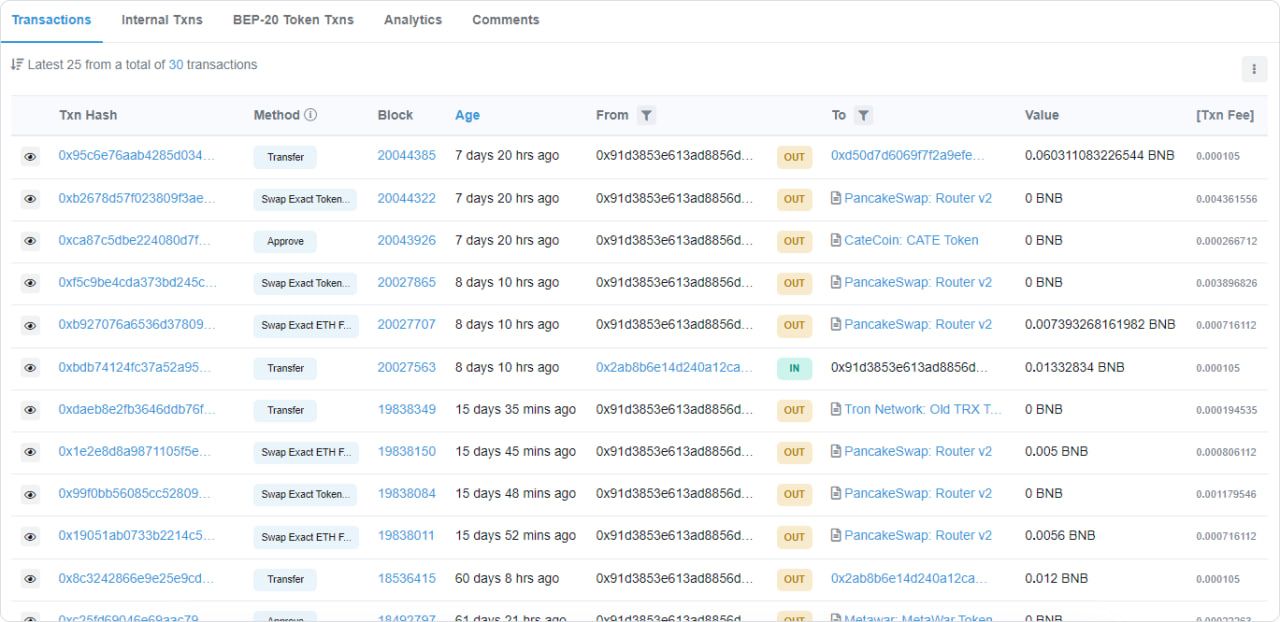
There would be numerous transactions occurring in quick succession, often within very short time frames. For instance, BNB (a native token play as gas fees) is transferred out almost immediately after being deposited.
This activity occurs because a script is constantly “checking” for incoming transfers to the wallet address and reacts nearly instantly by submitting a transaction to sweep the funds out.
5. To Keep Yourself Away From Honeypot Scams
Protecting yourself from honeypot scams requires a high level of skepticism, and a solid understanding of how smart contracts and blockchain technology work. Here are some strategies to help avoid falling victim to these scams:
5.1. Do Your Own Research (DYOR)
Before investing in any cryptocurrency, always conduct thorough research. This includes reviewing the project’s whitepaper, team background, social media channels, and community feedback. Look for warning signs such as anonymous developers, vague project goals, or aggressive marketing tactics.
Be especially cautious if a project promises guaranteed high returns with little to no risk, as this is often a red flag for a honeypot scam.
5.2. Check the Transaction History
Using blockchain explorers like Etherscan to analyze a contract’s transaction history can reveal important clues. Watch for unusual patterns, such as a high number of failed withdrawal attempts. A transaction history that suggests any transfers in are immediately moved out (or at least, shortly after) is also a red flag.
Honeypot scams often rely on scripts to quickly sweep funds into another wallet, that’s why checking for these patterns can help identify a honeypot scam.
5.3. Check the Smart Contract
If possible, examine the smart contract associated with the project. Platforms like Etherscan and BscScan allow users to view the contract’s code. Look for unusual conditions that may restrict selling or allow the contract owner to manipulate trading. If you are not familiar with reading code, consider using contract auditing services that can help identify potential honeypot traps.
5.4. Use Contract Analysis Tools
There are tools available, such as Honeypot.is and ScamSniffer, designed to detect honeypot scams by analyzing smart contracts. These honeypot scanners can simulate transactions and identify if there are conditions that would prevent you from selling the token. While these tools are not foolproof, they can provide an additional layer of protection.
5.5. Verify the Audit
Always check whether the smart contract has been audited. The risk of a honeypot scam is significantly reduced if the contract has undergone a thorough audit by a reputable company. If an audit is available, make sure to verify the credibility and ratings of the auditing firm to ensure its trustworthiness.
5.6. Avoid Anyone Sharing a Wallet
Be cautious of anyone who shares a seed phrase or Secret Recovery Phrase. This is a major red flag, as no legitimate user of a self-custodial wallet would ever disclose their recovery phrase. The only exceptions might be developers sharing access to a test wallet for specific purposes.
Conclusion
Honeypot scams present a significant risk to crypto investors by exploiting the lack of regulatory oversight and the complexity of blockchain technology. These scams are designed to look legitimate, using various tactics to trap unsuspecting victims. Stay vigilant, remain cautious, and always prioritize the safety of your funds over the lure of high returns.
Don’t forget to stay tuned with FMCPAY for more useful trading tips, trick & crypto insights!

